Although it's not recommended for large scale IPsec deployments because the Pre-Shared Key must be shared among users, IKEv1 with PSK and Xauth is an easy-to-deploy option and is well supported by mobile devices powered by iOS and Android. Moreover, IKEv2 is not supported by the built-in VPN client in Android yet.
In this tutorial, we'll install strongSwan 5.3.3 in openwrt 15.05, configure IKEv1 with PSK and Xauth, and finally setup the built-in VPN clients in Android and iOS so they can connect to it.
Installation
First of all, install necessary strongSwan packages in openwrt 15.05:
root@OpenWrt:~# opkg update
root@OpenWrt:~# opkg install strongswan-minimal strongswan-mod-xauth-generic
Configuration
To setup IKEv1 with PSK and Xauth, we only need to edit the following two configuration files.
/etc/ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
# strictcrlpolicy=yes
# uniqueids = no
# Add connections here.
conn %default
ikelifetime=60m
keylife=20m
rekeymargin=3m
keyingtries=1
conn roadwarrior
keyexchange=ikev1
left=%any
leftid=@openwrt.lan
leftsubnet=0.0.0.0/0
leftauth=psk
leftfirewall=yes
right=%any
rightauth=psk
rightauth2=xauth
rightsourceip=10.0.2.0/24
rightdns=10.0.0.1
auto=add
/etc/ipsec.secrets
# /etc/ipsec.secrets - strongSwan IPsec secrets file openwrt.lan %any : PSK "WhobByewg[cevHatyefunhevbydKeAv9" wenzhuo : XAUTH "Kagg#Od8"
We must choose strong PSK and passwords to ensure the security of IPsec connections. The example PSK and password shown above, which are generated using apg, are very good examples.
Firewall rules
If you want to connect from the WAN side, add the following configuration to /etc/config/firewall:
# allow incoming IPsec connections config rule option src wan option proto esp option target ACCEPT config rule option src wan option proto udp option dest_port 500 option target ACCEPT config rule option src wan option proto udp option dest_port 4500 option target ACCEPT config rule option src wan option proto ah option target ACCEPT
and then restart the firewall:
root@OpenWrt:~# /etc/init.d/firewall restart
Testing
Now stop the IPsec IKE daemon and restart it in foreground, so that we can immediately see its log messages on the ssh console:
root@OpenWrt:~# ipsec stop
root@OpenWrt:~# ipsec start --nofork
We can check the detailed information about established and configured connections by typing the ipsec status and statusall commands.
root@OpenWrt:~# ipsec status root@OpenWrt:~# ipsec statusall
Client Configuration
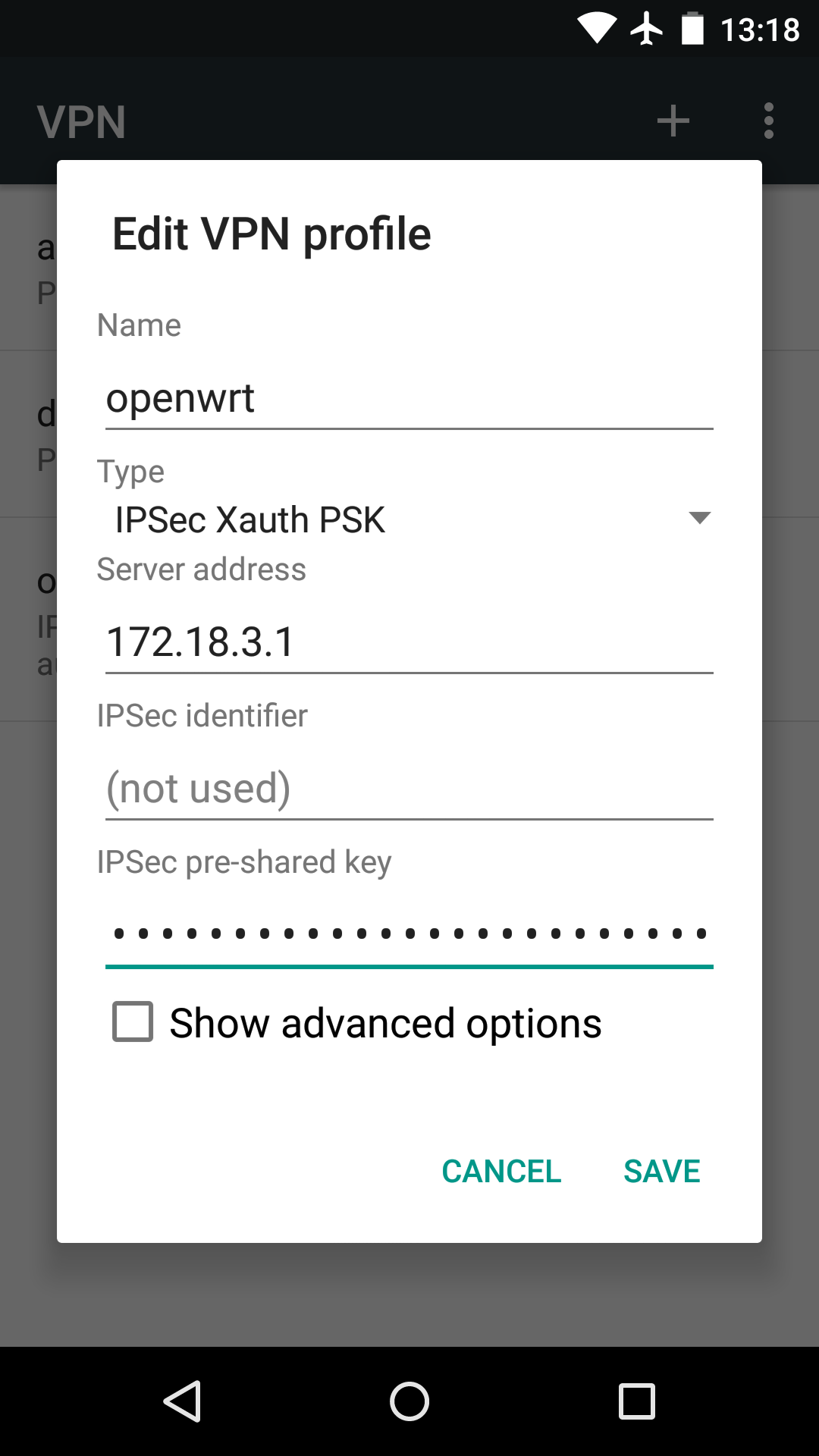
Android 5
Open Settings / Wireless & networks (... more) / VPN, tap the "+" sign in the upper-right corner of the Settings screen. On the Edit VPN profile dialog that pops up, enter the profile Name, select IPSec Xauth PSK in the Type drop-down menu, and then enter Server address and IPSec pre-shared key. Tap SAVE.
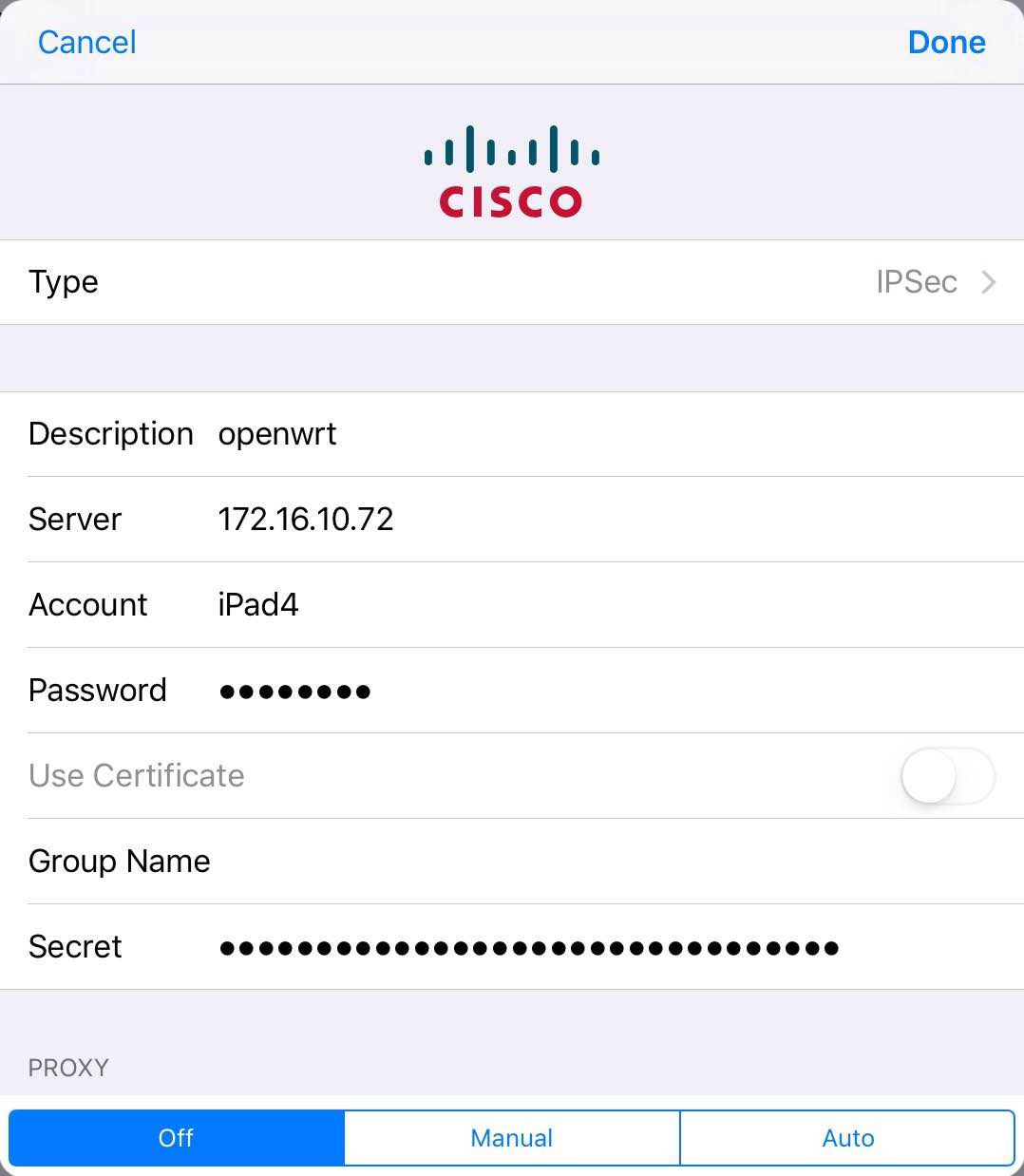
iOS 9
Open Settings / VPN, tap "Add VPN Configuration...". On the dialog that pops up, choose IPSec in the Type drop-down menu, and then tap Back. Enter all the necessary information: profile name in Descrption, server address in Server, username in Account, account password in Password and finally the PSK in Secret. Tap Done.
按照以上方法设置后,可以解析DNS,但是无法打开互联网,同时路由器内的其他计算机也ping不通,设置路由也如此。求教!
leftfirewall=yes?
搞定了,IP段分配的问题。低级错误。
我的ios10能连接vpn,能访问内网,不能访问外网,
ipsec status后 no files found matching ‘/etc/strongswan.d/*.conf’
rightdns=10.0.0.1没加上,谢谢你的资料
In addition to packages you mentioned you need to install
– kmod-ipsec
– iptables-mod-ipsec
They are package dependencies of strongswan-minimal and others
# opkg update
# opkg whatdepends kmod-ipsec
Yes right, i mean you need to update the doc 🙂
On this I agree with you. But you can do it yourself and post your own blog 😉 This article deals with openwrt 15.05 only
And there is no port forwarding in configuration
Not necessary for a WAN-facing router
The problem is – when you connecting to the router – it connects but traffic is not going through. At least DNS doesn’t work.
“leftfirewall=yes” handles forwarding for IPsec peers