The interoperability of IPsec implementations on various platforms has been becoming better and better over the last few years. For example, Windows 7 and newer releases fully support the IKEv2 (RFC 4306) and MOBIKE (RFC 4555) standards, and iOS started to support configuration of IKEv2 in the GUI since version 9.0.
In this tutorial, we'll install strongSwan 5.3.3 in openwrt 15.05, configure it to provide IKEv2 service with public key authentication of the server and username/password based authentication of the clients using EAP-MSCHAP v2, and finally setup the VPN clients in Windows, Android and iOS so they can connect to it. Much of the complexity of IKEv2 configuration lies in the creation of SSL certificates.
Installation
First of all, install necessary strongSwan packages in openwrt 15.05:
root@OpenWrt:~# opkg update
root@OpenWrt:~# opkg install strongswan-minimal strongswan-mod-eap-mschapv2 strongswan-mod-eap-identity strongswan-mod-constraints strongswan-mod-md5 strongswan-mod-pem strongswan-mod-pkcs1 strongswan-mod-revocation
Creating CA and server certificates
I recommend using XCA to create and maintain your root CA for your IKEv2 service. iOS silently refuses to trust CA certificates with MD5 signatures. So make sure to create CA certificates with SHA1, or better SHA256, signatures. Export your CA certificate in DER format. In the configuration example below, our CA cert is exported as file ZhangsRootCA2.cer. You are advised to upload the CA certificate to a secured web server or mail it to your own E-mail accounts.
Different IPsec implementations have different requirements on the server certificate. See the strongSwan wiki article for details. These requirements can be satisfied in XCA by making the following changes to a new certificate based on its HTTPS_server template:
- Add "IP security end entity" to "X509v3 Extended Key Usage" attribute.
-
Add all domain names and IP addresses of the IPsec server to the "X509v3 Subject Alternative Name" in the type of DNS and IP. IP addresses can be added to the SAN attribute as both DNS and IP to achieve best compatibility.
Here are the important details of an example IPsec server certificate created using XCA:
commonName: openwrt
X509v3 Extended Key Usage: TLS Web Server Authentication, IP security end entity
X509v3 Subject Alternative Name: DNS:openwrt, DNS:openwrt.lan, DNS:ipsec.example.com, DNS:192.168.1.1, DNS:10.8.0.1, IP Address:192.168.1.1, IP Address:10.8.0.1
Netscape Cert Type: SSL Server
Export the server cert and the server key as openwrt.cer and openwrt.der respectively. The server key should only be stored in openwrt.
Configuration
Certificates
- Save the CA certificate in folder /etc/ipsec.d/cacerts/.
-
Save the server key as /etc/ipsec.d/private/openwrt.der. Change the file permission of the key file to 0600:
# chmod 0600 /etc/ipsec.d/private/*
- Save the server certificate as /etc/ipsec.d/certs/openwrt.cer.
/etc/ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
# strictcrlpolicy=yes
# uniqueids = no
uniqueids=never
conn roadwarrior-ikev2
keyexchange=ikev2
dpdaction=clear
dpddelay=60s
dpdtimeout=300s
rekey=no
left=%any
leftid=openwrt
leftcert=openwrt.cer
leftauth=pubkey
leftsendcert=always
leftsubnet=0.0.0.0/0
leftfirewall=yes
right=%any
rightauth=eap-mschapv2
rightsourceip=<CIDR>
rightdns=<DNS.Server>
eap_identity=%identity
auto=add
Note: rightsourceip can specify an IP address pool in the form of CIDR notation. rightdns specifies the IP address of the DNS server that the IPsec clients should use.
/etc/ipsec.secrets
# /etc/ipsec.secrets - strongSwan IPsec secrets file
: RSA openwrt.der
Username : EAP "PASSWORD"
Firewall rules
If you want to connect from the WAN side, add the following configuration to /etc/config/firewall:
# allow incoming IPsec connections
config rule
option src wan
option proto esp
option target ACCEPT
config rule
option src wan
option proto udp
option dest_port 500
option target ACCEPT
config rule
option src wan
option proto udp
option dest_port 4500
option target ACCEPT
config rule
option src wan
option proto ah
option target ACCEPT
and then restart the firewall:
root@OpenWrt:~# /etc/init.d/firewall restart
Circumventing the PMTUD Problem
It's a common practice in IPsec implementations to set the MTU of the IPsec tunnel interface to 1400 or lower. You won't experience Path MTU Discovery problems if the MTU of your WAN interface is standard, which is 1500 in the case of Ethernet, or 1492 in the case of PPPoE. However, if the MTU of your WAN interface is significantly lower than 1500, you need to set the MTU of the installed routes for IPsec clients to a value lower than 1400, which can be achieved using the strongswan kernel-netlink module.
The MTU of my PPPoE WAN interface is 1442. To prevent IPsec clients from running into PMTUD problems, I have to change the mtu option in /etc/strongswan.d/charon/kernel-netlink.conf to around 1350:
# MTU to set on installed routes, 0 to disable.
mtu = 1352
Testing
Now stop the IPsec IKE daemon and restart it in foreground, so that we can immediately see its log messages on the ssh console:
root@OpenWrt:~# ipsec stop
root@OpenWrt:~# ipsec start --nofork
After testing is done, interrupt the ipsec start --nofork command by pressing Ctrl-C and start ipsec again by typing the following command:
root@OpenWrt:~# ipsec start
We can check the detailed information about connections by typing the ipsec status and ipsec statusall commands.
root@OpenWrt:~# ipsec status
root@OpenWrt:~# ipsec statusall
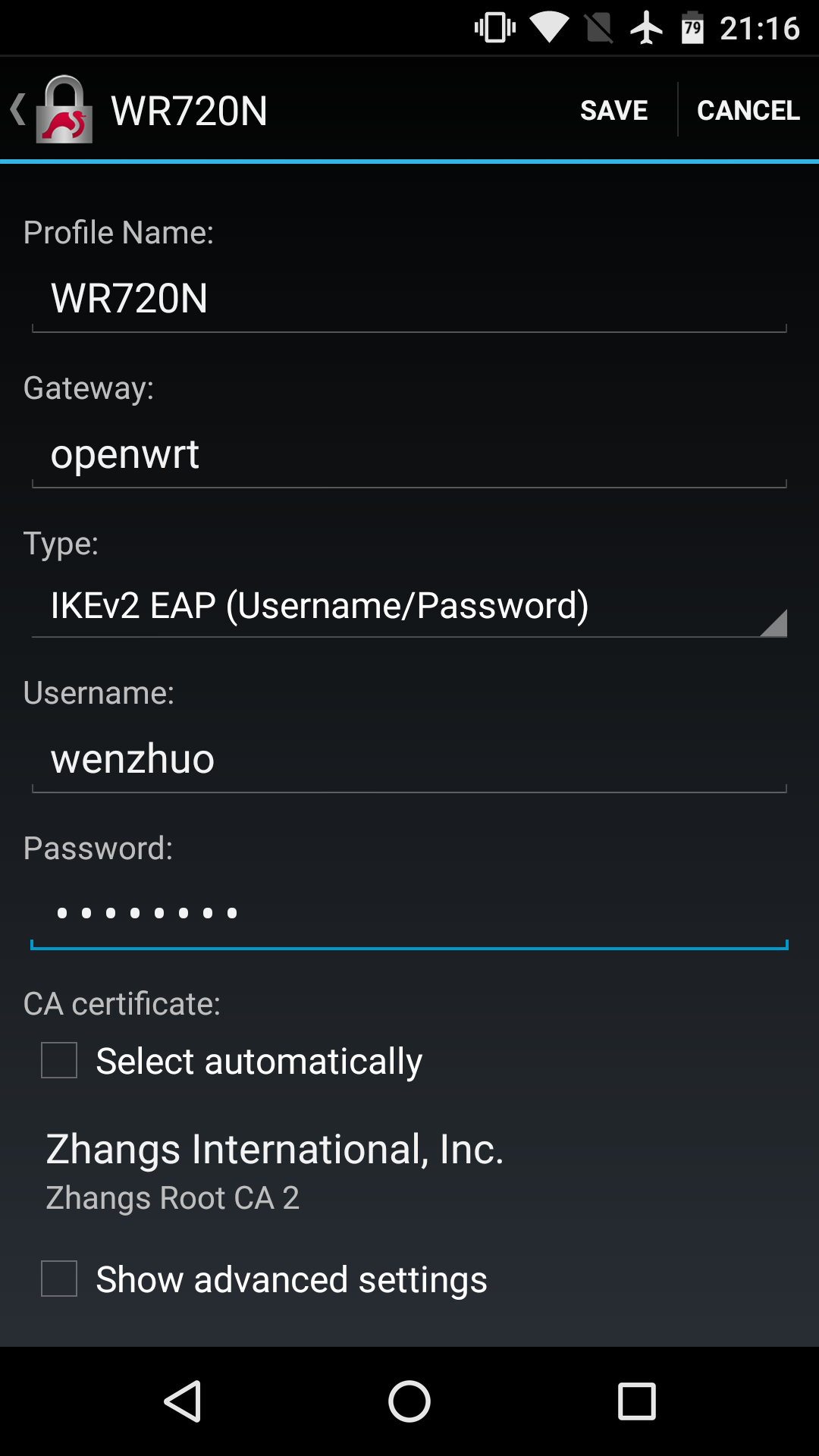
Client Configuration
Android 5+
- Install the official strongSwan app.
-
Import the CA certificate ZhangsRootCA2.cer. When opening the certificate, you'll be prompted whether to open with the android "Certificate Installer" or the strongSwan "Import certificate" utility. If you're using the CA certificate for IPsec only, you may import it to the strongSwan app, instead of the system certificate store of your Android device.
-
Open the strongSwan app, and tap ADD VPN Profile.
-
Edit the profile as follows. Uncheck the Select automatically option under "CA certificate:" and manually select the CA certificate we just imported. Tap Save.
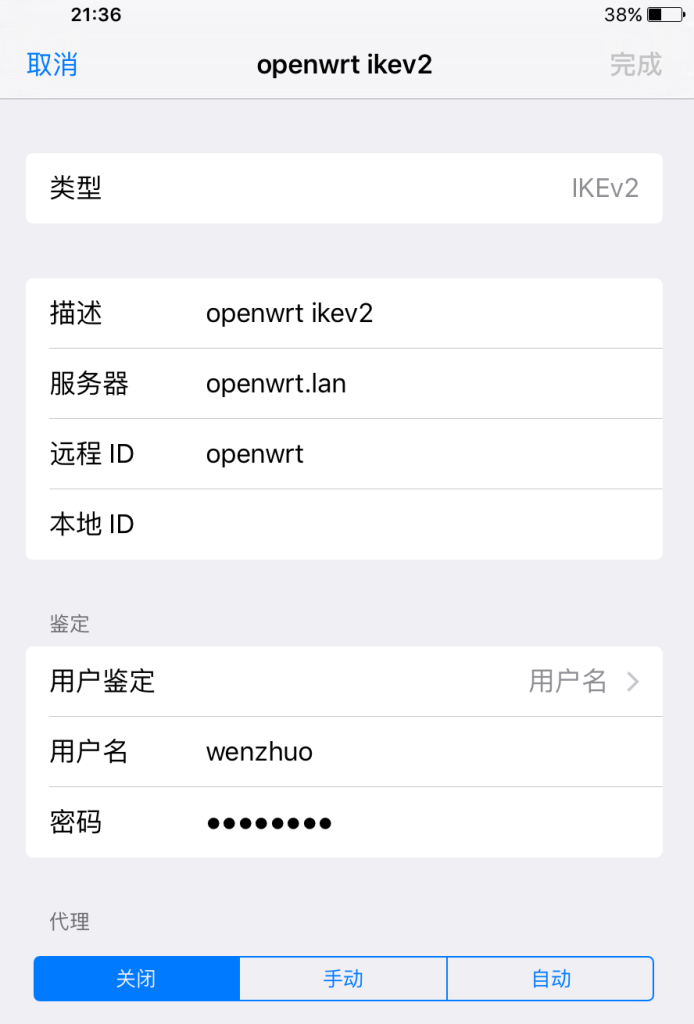
iOS 9+
- Import the CA certificate. As of iOS 9.2.1, a reboot is apparently necessary for the certificate import to take effect.
-
Open Settings / VPN, tap Add VPN Configuration.... Enter all the necessary information as follows, and then tap Done.
Description: Profile name
Server: Server Address
Remote ID: commonName (CN) of Server Certificate
Username: Username
Password: Password
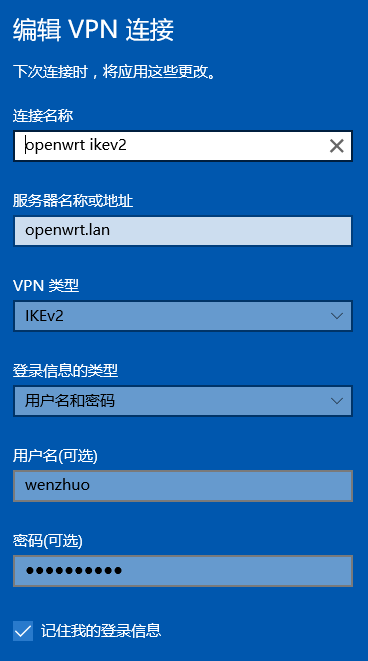
Windows 10
- Import the CA certificate to the system certificate store:
Double-click the certificate file, click Open and then Install Certificate.... You must choose Local Computer as Store Location. On the Certificate Store popup, choose the option Place all certificates in the following store. Click Browse... and choose the Trusted Root Certification Authorities / Certificates folder. Click Next and then Finish to complete the certificate import.
-
Click the Windwos Start menu / Settings / Network and Internet / VPN / Add VPN Connection. Enter information as shown in the following screenshot. Click Save.
-
By default, Windows 10 IPsec client adds a route to the remote network based on its IPv4 address class. If you want to set the default gateway on the remote network, you need to change the adapter settings of the VPN connection:
On the Network and Internet / VPN settings page, click Change Adapter Settings. Right-click the VPN connection you just created and then click Properties / Networking tab / Internet Protocol Version 4 (TCP/IPv4) / Properties / Advanced(V).... On the Advanced TCP/IP Properties dialog, check Use default gateway on the remote network. Click the OK buttons to close the configuration dialogs you just opened.
Note: Although Windows 10 can successfully get the remote DNS server addresses when establishing IPsec connections, it keeps querying the local DNS servers for resolving domain names. This can cause connectivity issues for GSLB (Global Server Load Balancing) domain names and those domain names under DNS-poisoning attacks. In such cases, you're strongly advised to use a http proxy or a socks5 proxy server on the remote network.
Ubuntu 18.04
The NetworkManager strongswan plugin hasn't improved much over the years. It doesn't work with EAP-MSCHAPv2 and its pre-shared key option doesn't even include an input box for the key. We'll have to stick with file-based configuration in Ubuntu 18.04.
- Install necessary packages:
$ sudo apt update $ sudo apt install strongswan libcharon-extra-plugins - Edit /etc/ipsec.conf:
config setup # strictcrlpolicy=yes # uniqueids=no conn WR720Nv2 left=<Own.Address> leftsourceip=%config4 leftfirewall=yes leftauth=eap-mschapv2 eap_identity=<Username> right=<Server.Address> rightauth=pubkey rightid=openwrt rightsubnet=<Subnet> auto=start - Put your password in /etc/ipsec.secrets:
Username : EAP "PASSWORD" - Save the CA certificate file in folder /etc/ipsec.d/cacerts.
-
Reload the IKE daemon:
$ sudo ipsec reload
As with the server configuration in OpenWrt, you can use commands ipsec status and ipsec statusall to check your connection status.
在Use default gateway on the remote network下面,把interface metric手动设为15,应该可以解决DNS问题。Win10真是一团渣。
用XCA制作的证书导出格式只有.cer和.crt,没有.der的选项,怎么办??
.der是私钥文件,应该在Private Keys选项卡中导出。
感谢!现在证书的问题搞定了,但是还有一个问题,我想同一个账号多个终端同时使用,/etc/config/firewall中rightsourceip=的格式改怎样写呢?我现在写成rightsourceip=192.168.100.20-30是不行的。
CIDR形式,如 192.168.100.192/27
uniqueids = yes | no | never | replace | keep
whether a particular participant ID should be kept unique, with any new IKE_SA using an ID
deemed to replace all old ones using that ID. Participant IDs normally are unique, so a new
IKE_SA using the same ID is almost invariably intended to replace an old one.
The difference between no and never is that the daemon will replace old IKE_SAs when receiving an
INITIAL_CONTACT notify if the option is no but will ignore these notifies if never is configured.
The daemon also accepts the value replace which is identical to yes and the value keep to reject
new IKE_SA setups and keep the duplicate established earlier.
以上几种参数都试过了,但是为什么就是同一id在不同终端上重复拨号分配不到不同的IP呢?只能最后一个拨号的上网。
uniqueids=never就可以了。记得重载配置文件:ipsec reload
你好,可以请“Creating CA and server certificates”,的操作命令列出来吗?
XCA是GUI程序。制作证书的要点我已列出,具体操作请自行阅读XCA的帮助文档。;)
I can connect and ping the right hand virtual ip, but I do not see traffic coming back from my IOS10 phone.
your config was very helpful, though I use letsencrypt public free certificates.
Make sure rightsouceip is a subnet of your LAN, in CIDR format, and leftfirewall=yes.
大哥,windows7连不上,客户端证书到地怎么做啊?我服务器证书:C=CN O=DIR505_VPN CN=DIR505_Root_CA,客户端:C=CN O=DIR505_VPN CN=CLIENT@DIR505,不行呢!!此外修改注册表HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\RasMan\Parameters\
也不行,请赐教!
应该是证书属性的问题。请严格按照说明制作证书。
Win7证书问题已解决,多谢!
export the server key as public or private der?
Xca exports key as .der and certificate as .cer
Thanks for the reply, there are options called “Der Public(.der)” and “Der Private(.der)” available. Both are in .der.
and XCA version is 1.3.2.
Tried both .der formats. No success. Something else must be wrong. But to make the key is right first.
I was using xca ver. 1.1.0 when writing the article. It provides two options only for exporting keys: PEM and DER. As for the latest version, you should obviously choose DER private, according to its latest documentation: http://xca.sourceforge.net/xca-7.html#ss7.2
Many thanks. Finally get iOS connected. Your tutorial is complete.
Turns out the racoon service on my stock openwrt is alive and un-configed. It intercepts each incoming VPN connection request before strongswan.
大神,到底能不能让我提问啊?我可是怀着崇拜的心情来的啊
刚看到你的评论。本网站是用wordpress搭建的个人博客网站;为防止网络小广告,启用了captcha和wp-spamshield模块,而且新用户第一个评论必须通过人工审核。
实在无法提问,一直说垃圾内容.你这样会丢失多少和网友的互动啊
又删帖了,你到底是怎么想的啊?
我没删过贴。wp-spamshield插件有问题,会导致未登录用户留言500 Internal Server Error;我刚把它停用了。
的确不提示垃圾留言了,但评论还是无法提交
你又换了一个Email地址,留言是成功的,第一条留言待审。
好的.首先感谢您的分享.
其次请教您一个问题,我按照您的方法配置完成,唯一的不同就是我的证书不是自签发的,而是购买的证书,原因是:
我在国外的VPS上部署了IKEv2/IPSec并且购买了comodorsa的证书,运行一切OK,所以证书肯定是没问题的.考虑到国内的VPS贵且家里现成的宽带可以利用,所以才打算在OpenWRT上安装IKEv2/IPSec服务器.
另外就是mtu没改
证书拷贝如下:
ca.cert.pem拷入/etc/ipsec.d/cacerts/
server.cert.pem和client.cert.pem拷入/etc/ipsec.d/certs/
server.pem和client.pem拷入/etc/ipsec.d/private/
/etc/ipsec.conf内容如下:
config setup
uniqueids=never
conn iOS_cert
keyexchange=ikev1
fragmentation=yes
left=%defaultroute
leftauth=pubkey
leftsubnet=0.0.0.0/0
leftcert=server.cert.pem
right=%any
rightauth=pubkey
rightauth2=xauth
rightsourceip=10.31.2.0/24
rightcert=client.cert.pem
auto=add
conn android_xauth_psk
keyexchange=ikev1
left=%defaultroute
leftauth=psk
leftsubnet=0.0.0.0/0
right=%any
rightauth=psk
rightauth2=xauth
rightsourceip=10.31.2.0/24
auto=add
conn networkmanager-strongswan
keyexchange=ikev2
left=%defaultroute
leftauth=pubkey
leftsubnet=0.0.0.0/0
leftcert=server.cert.pem
right=%any
rightauth=pubkey
rightsourceip=10.31.2.0/24
rightcert=client.cert.pem
auto=add
conn ios_ikev2
keyexchange=ikev2
ike=aes256-sha256-modp2048,3des-sha1-modp2048,aes256-sha1-modp2048!
esp=aes256-sha256,3des-sha1,aes256-sha1!
rekey=no
left=%defaultroute
leftid=My Domain
leftsendcert=always
leftsubnet=0.0.0.0/0
leftcert=server.cert.pem
right=%any
rightauth=eap-mschapv2
rightsourceip=10.31.2.0/24
rightsendcert=never
eap_identity=%any
dpdaction=clear
fragmentation=yes
auto=add
conn windows7
keyexchange=ikev2
ike=aes256-sha1-modp2048!
rekey=no
left=%defaultroute
leftauth=pubkey
leftsubnet=0.0.0.0/0
leftcert=server.cert.pem
right=%any
rightauth=eap-mschapv2
rightsourceip=10.31.2.0/24
rightsendcert=never
eap_identity=%any
auto=add
/etc/ipsec.secrets内容如下:
: RSA server.pem
: PSK “mysecurepsk”
: XAUTH “mysecurepsk”
Test %any : EAP “Test”
测试前先用虚拟机里的Win7(NAT方式上网)连了我的国外VPS,连接成功,说明客户端配置OK.然后修改hosts文件,将192.168.200.1对应我的那个域名,以便强制客户端连接OpenWRT的IKEv2/IPSec服务器,结果连不上,Win7提示13801错误: IKE authentication credentials are unacceptable
检查OpenWRT上的输出,显示:
10[NET] received packet: from 192.168.200.2[1000] to 192.168.200.1[500] (528 bytes)
10[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
10[IKE] 192.168.200.2 is initiating an IKE_SA
10[IKE] remote host is behind NAT
10[IKE] sending cert request for “C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO RSA Domain Validation Secure Server CA”
10[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(MULT_AUTH) ]
10[NET] sending packet: from 192.168.200.1[500] to 192.168.200.2[1000] (333 bytes)
07[NET] received packet: from 192.168.200.2[4298] to 192.168.200.1[4500] (484 bytes)
07[ENC] parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ]
07[IKE] received 8 cert requests for an unknown ca
07[CFG] looking for peer configs matching 192.168.200.1[%any]…192.168.200.2[192.168.222.7]
07[CFG] selected peer config ‘ios_ikev2’
07[IKE] initiating EAP_IDENTITY method (id 0x00)
07[IKE] peer supports MOBIKE
07[LIB] hash algorithm HASH_SHA256 not supported
07[IKE] authentication of ‘My Domain’ (myself) with RSA signature successful
07[IKE] sending end entity cert “OU=Domain Control Validated, OU=PositiveSSL, CN=My Domain”
07[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ]
07[NET] sending packet: from 192.168.200.1[4500] to 192.168.200.2[4298] (1732 bytes)
(过了十几秒后)
14[JOB] deleting half open IKE_SA after timeout
另外,发现我在输入ipsec restart时,提示
Stopping strongSwan IPsec…
no files found matching ‘/etc/strongswan.d/*.conf’
Starting strongSwan 5.3.2 IPsec [starter]…
我将ipsec.conf复制到/etc/strongswan.d/,再运行ipsec restart,提示
Stopping strongSwan IPsec…
/etc/strongswan.d/ipsec.conf:1: syntax error, unexpected NAME, expecting NEWLINE or ‘{‘ or ‘=’ [setup]
invalid config file ‘/etc/strongswan.conf’
Starting strongSwan 5.3.2 IPsec [starter]…
麻烦帮忙看一下问题原因,谢谢!
日志显示win7连接时选中的连接配置是ios_ikev2,建议你把ike、esp加密套件注释掉试试,或者按照https://wiki.strongswan.org/projects/strongswan/wiki/Win7EapMultipleConfig设置。另,/etc/ipsec.conf不能移到strongswan.d目录下。
加密套件注释掉了,那岂不是不安全了?
我之前试过把ios_ikev2的删掉,还是不行,只是日志忘了弄下来了
不会不安全,strongswan会接受win7提出的加密套件。你的日志里有条信息:“07[LIB] hash algorithm HASH_SHA256 not supported”,应该是你设定了加密套件造成的。
那对于ios来说,没有了HASH_SHA256,也是个隐患了吧
注释掉了,还是报错,算了,不管了,反正已经装好了,最好的安装方式其实就两句话:
opkg install strongswan-full openssl-util
另外,关于端口映射的问题,因为服务器在内网,我映射了UDP 500和4500,但是服务器上的日志完全没反应,也连不上,有什么办法吗?
你的路由器存储空间可能比较大,别人4M/8M闪存就得省着点用,能不装就不装了。
如果你的网关操作系统内核是Linux,可以用以下命令设置端口转发:
一步一步按照您的步骤,路由器是R2S的openwrt系统
开始调试就出现了这个
root@OpenWrt:~# ipsec start –nofork
Starting strongSwan 5.9.1 IPsec [starter]…
00[DMN] Starting IKE charon daemon (strongSwan 5.9.1, Linux 5.4.102, aarch64)
00[KNL] unable to create netlink socket: Protocol not supported (93)
00[NET] installing IKE bypass policy failed
00[NET] installing IKE bypass policy failed
00[NET] enabling UDP decapsulation for IPv6 on port 4500 failed
00[NET] installing IKE bypass policy failed
00[NET] installing IKE bypass policy failed
00[NET] enabling UDP decapsulation for IPv4 on port 4500 failed
00[LIB] feature CUSTOM:libcharon in critical plugin ‘charon’ has unmet dependency: CUSTOM:kernel-ipsec
00[CFG] loading ca certificates from ‘/etc/ipsec.d/cacerts’
00[CFG] ca certificate “” lacks ca basic constraint, discarded
00[CFG] loading ca certificate from ‘/etc/ipsec.d/cacerts/openwrt_strongswan.cer’ failed
00[CFG] loading aa certificates from ‘/etc/ipsec.d/aacerts’
00[CFG] loading ocsp signer certificates from ‘/etc/ipsec.d/ocspcerts’
00[CFG] loading attribute certificates from ‘/etc/ipsec.d/acerts’
00[CFG] loading crls from ‘/etc/ipsec.d/crls’
00[CFG] loading secrets from ‘/etc/ipsec.secrets’
00[LIB] building CRED_PRIVATE_KEY – RSA failed, tried 4 builders
00[CFG] loading private key from ‘/etc/ipsec.d/private/openwrt_strongswan.der’ failed
00[CFG] loaded EAP secret for Username
00[LIB] failed to load 1 critical plugin feature
00[DMN] initialization failed – aborting charon
charon has quit: initialization failed
charon refused to be started
ipsec starter stopped
root@OpenWrt:~#
根据日志判断可能有两方面的问题:一缺内核模块xfrm_user;二加载的CA证书错误,openwrt_strongswan.cer应该是openwrt_strongswan.der对应的服务器证书,不是CA证书。
谢谢回复,重新按照教程,折腾了两天最终实现了ios连通openwrt路由器。
联通后,可以播放nas里的音视频。到这儿,又遇到一个新的问题,手机访问局域网里的设备都没问题。未解决的问题是如何让手机通过家里的路由器出国,还请指点迷津。
之前测试有误,其实只要映射500和4500端口就可以连上了,很神奇,居然不需要映射eap,不过必须是linux路由器才可以,普通路由器映射了500和4500也不行.
但有个问题,Win7连上后,无法上网,这是为何?
我有两级路由,第一级是装了SS的TT(WAN: PPPoE拨号动态IP, LAN: 192.168.2.1),DMZ到二级路由(WAN: 静态192.168.2.2, LAN: 10.10.10.1),二级路由也是TT,应该可以映射esp,之所以需要两级,是因为SS和OpenVPN冲突,所以只能分开.
现在IKEv2/IPSec服务器(WAN: 静态10.10.10.93, LAN: 192.168.200.1)是挂在二级路由器的下面,UDP端口映射没问题,二级路由器也可以映射esp报文,那一级路由器上是否也要做映射?光DMZ够不够?
这样的网络环境下,IKEv2/IPSec服务器的mtu还需要改吗?
另外,无法上网的原因会是啥?毕竟在服务器端,可以ping通客户端的IP.
谢谢!
如果通过NAT,ESP报文就会被封装在UDP/4500报文里,无ESP映射不要紧。但是你的Win7和openwrt都在局域网,IPSec连接未穿透NAT,有很大可能是因为ESP协议类型的报文没被允许通过,造成win7可以连接,但无法上网。
MTU需不需要改主要看你的宽带PPPoE的MTU。如果有些网站可以上有些不行,或者同一个网页上部分内容无法打开,那就很有可能碰到了PMTU-D问题。
这些和本文相关。你的网络结构比较复杂,其他具体联网问题,须靠你自己解决。
Win7在局域网肯定没问题的,因为这就像在路由器下面一样,没听说哪个手机/电脑在一个或多个路由器下就不能连接VPN服务器了,对吧.
我的openwrt虽然也在内网,但500和4500端口都做了映射(或者叫转发)了啊.也不行吗?
IPSec连接如果穿透NAT,会把ESP报文封装在UDP/4500报文里,所以不需要防火墙规则允许ESP报文通过。如果两端都在LAN上或者路径中无NAT,则需要保证防火墙规则允许ESP协议报文通过。你按照本文Firewall Rules一节操作了吗?这是你碰到的Win7能建立连接,却无法上网最可能的原因。如果不是这个问题,我建议你用tcpdump/wireshark抓包进一步分析。
封装在4500里,那就相当于隧道模式了吧?
我的firewall是完全按照你文中写的来的
config rule
option src wan
option proto esp
option target ACCEPT
config rule
option src wan
option proto udp
option dest_port 500
option target ACCEPT
config rule
option src wan
option proto udp
option dest_port 4500
option target ACCEPT
config rule
option src wan
option proto ah
option target ACCEPT
即使从LAN口连接服务器,也不能上网,我觉得这跟防火墙关系应该也不大了…
顺便说一下,普通路由器映射500,4500根本不行,TT只映射这两个端口立马连上
能否将路由器当作客户端,额外需要什么配置?
当然可以的,而且更简单,不会有兼容性问题。具体配置请查阅strongswan官网文档。
吾辈读书之人,看帖焉能不回?
好贴就要气沉丹田,力贯头顶,
用力一顶!
大佬,实在是不会openwrt下ikev2的客户端,官网一片英文用chrome翻译也是头晕,能否给些地址学习一下.不是自己不找,是真心google搜索出来几乎都是服务器端,没啥客户端资料啊.
本文Ubuntu 18.04一节有strongswan客户端配置。都是strongswan ipsec.conf配置,跟OpenWrt一样的;但安装包须按照本文开头openwrt的。
谢谢你的教程。
请教一下,我这里按教程走完后,再添加了一条规则:
iptables -t nat -A POSTROUTING -s 10.0.1.0/24 -d 10.0.0.0/24 -j MASQUERADE
其中,路由是 10.0.0.0/24,虚拟IP是10.0.1.0/24。最后表现是从虚拟IP 10.0.1.1 去ping 路由(10.0.0.1)和路由背后的设备(10.0.0.2)都能通,但如果是访问网页(路由配置界面)或共享的话,10.0.0.2能访问,路由却是访问不了的,请问这是正常表现吗?我可以怎样排查一下?
应该是路由器上web service的访问控制问题——不允许10.0.1/24访问。你的ipsec服务好像就是运行在路由器上,这条masquerade规则是不必要的。
非常感谢这么快回复和帮助。
ipsec服务确实是运行在路由器上,10.0.0.1
10.0.0.2 是个当交换机用的路由。
两个路由都有web配置页面,也都挂了共享。
现在的表现不止是 WEB 访问不了,挂在路由器上的共享也访问不了。并且masquerade不配置的话,连10.0.0.2也访问不了(不论web还是共享)。
如果是web service的访问控制问题,应该去哪配置呢?
conn roadwarrior-ikev2
keyexchange=ikev2
dpdaction=clear
dpddelay=300s
rekey=no
left=%any
leftid=openwrt
leftcert=openwrt.cer
leftauth=pubkey
leftsendcert=always
leftsubnet=0.0.0.0/0
leftfirewall=yes
right=%any
rightauth=eap-mschapv2
rightsubnet=10.0.1.0/24
rightsourceip=10.0.1.0/24
rightdns=114.114.114.114
eap_identity=%any
auto=add
这是路由上的配置。本来想rightdns配置成10.0.0.1的,因为这样可以防DNS污染。但这样外网也上不了。说明不止是web和共享,连dns的包也到不了10.0.0.1,不管加不加masquerade都到不了
再补充一下,没有masquerade情况下 , “tcpdump host 10.0.1.1” 抓包的信息,抓包显示,我在客户端访问各种地址,只有“10.0.1.1.53319 > 10.0.0.2”能抓到,看起来,除了访问.2能进来,其他.1, .10, .90什么的都不行的感觉。但我也不会配置过这种奇怪的规则啊
06:04:22.455447 IP 10.0.1.1.53319 > 10.0.0.2.www: Flags [S], seq 1316982133, win 65535, options [mss 1360,nop,wscale 6,nop,nop,TS val 462145554 ecr 0,sackOK,eol], length 0
如果有masquerade,就一条也抓不到了,可能来源IP已经被改了
最后经过各种试验,终于改到能访问,但不知是否有安全隐患。
firewall 区域配置里,wan 的输入和转发原先是拒绝的,改成接受。
config zone
option name ‘wan’
list network ‘wan’
list network ‘wan6’
option output ‘ACCEPT’
option masq ‘1’
option mtu_fix ‘1’
option input ‘ACCEPT’ #’REJECT’
option forward ‘ACCEPT’ #’REJECT’
这时不用masquerade,客户端就能访问.1了。但.2不行,还是要加上 masquerade 才能:
iptables -t nat -A POSTROUTING -s 10.0.1.0/24 -d 10.0.0.0/24 -j MASQUERADE
所以主要变动就是wan区域的2个拒绝变接受就成功了,请问有什么隐患吗?
如果wan是Internet,不可把缺省策略改成ACCEPT。两端都在局域网上,直接路由可达,能不用额外添加一条NAT规则,就别添加。
变成在这里直播解决问题了…😅
最后做法是保持 wan 入站数据拒绝状态,但允许 `10.0.1.0/24` 来源的包。但允许的规则要优先于默认的拒绝规则:
iptables -I INPUT 1 -s 10.0.1.0/24 -j ACCEPT
iptables -t nat -A POSTROUTING -s 10.0.1.0/24 -d 10.0.0.0/24 -j MASQUERADE
精神可嘉,但是:1)向别人请教,须先把问题描述清楚,在你这个网络问题上须描述清楚网络结构,画张拓扑图;2)标准的openwrt做法是定义区域(zone),防火墙设置请查阅openwrt官网文档。
嗯,多谢指教,一直都是自己摸索惯了,初次来问问题,没有经验😁
再次感谢你的指点。已经切换成 zone的方式来配置防火墙。实际使用中,因为 Strongswan 无法区分位于同一个 NAT 背后的多个设备(https://wiki.strongswan.org/issues/365#note-1)。因此,同一局域网多台设备同时登录时,不管是否用同一账户,都会导致之前登录的用户无法连接网络。
我的 openwrt版本是14.07,软件包的 Strongswan 版本是 5.32,不知道博主这边有什么解决方案,或有关这方面的新消息吗?
这是l2tp传输模式的问题。IKEv2没有此问题,多设备同时穿透NAT妥妥的。
抱歉,看来链接那篇文章和我的问题看来不是同一个。 我严格按你的配置做的,客户端创建的类型也是 IKEv2。
我想达到的结果是,用同样的配置(账号密码证书),多台设备同时连接到路由都能正常工作。
现在的情况是, ipsec.conf 中只配置了一个链接,不管是不是同一个NAT下,如果2台设备同时连接,能各自得到IP,只是:
第2台设备一连接,第1台就没网络(也不会被踢出)
第2台一退出,第1台又会恢复正常。
Debug 消息也看不出什么,网上有说不同设备连到同一配置的,要用 EAP-radius什么的,我不置可否,没有radius服务器可以试验,这个问题实在不知道怎么查资料,只好又来麻烦你了。
以下是ipsec.conf :
config setup
uniqueids = never
charondebug=”ike 2, knl 0, cfg 0″
conn roadwarrior-ikev2
keyexchange=ikev2
dpdaction=clear
dpddelay=300s
left=%any
leftid=openwrt
leftcert=openwrt.cer
leftauth=pubkey
leftsendcert=always
leftsubnet=0.0.0.0/0
leftfirewall=yes
right=%any
rightauth=eap-mschapv2
rightsubnet=10.0.1.0/24
rightsourceip=10.0.1.0/24
rightdns=10.0.0.1
eap_identity=%any
auto=add
应该是你自己添加的rightsubnet惹的祸
果然如此👏。我排查了一天一夜没结果,博主一眼就看出来了,真是达到了炉火纯青的地步👍👍。非常感谢!!!
最后发现真是被rightsubnet 这个给坑死了。正如你之前留言说所说的,masquerade 是不需要的。我也奇怪为什么我不NAT就行,才搞出了这几天的事,又NAT又Zone的,去掉这句就什么都不用做。
我也不知在其他什么地方看到这句,还说要跟rightsourceip是一个网段什么的,字面上看起来很和谐的配置,想不到是个巨坑。
再次感谢!